Organizations must consider user and device identity as part of their security strategy to protect sensitive data and maintain control over access to resources in the modern era of cybersecurity. Microsoft Entra Conditional Access policies provide organizations with the ability to enforce identity-driven access controls.
Understanding Conditional Access policies
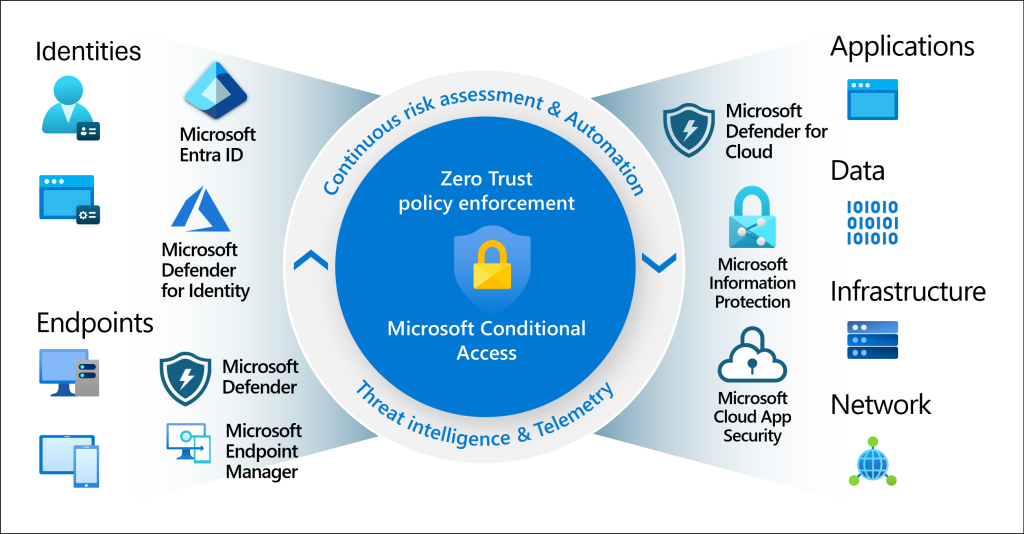
Conditional Access policies serve as if-then statements that determine access requirements based on specific conditions. For example, an organization can enforce multi-factor authentication (MFA) as a prerequisite for accessing sensitive resources or require specific device, location, or application context criteria for accessing applications. Administrators can create fine-grained access controls by leveraging various signals, such as:
– User or group membership
– IP location information
– Device state
– Application context
These signals allow administrators to target specific users and groups, cloud applications, user actions, or authentication contexts, giving them fine-grained control over access policies. Conditional Access policies are enforced after first-factor authentication is completed and can be integrated with user flows and custom policies.
Advanced Conditional Access policy options
Previously, we mentioned a policy that requires MFA for users accessing sensitive resources, but there are several other advanced policy options available to organizations. Let’s explore a few of the commonly used policies:
Requiring MFA for administrators:
To reduce the risk of compromise, it is recommended to enforce MFA on administrative accounts since they are often targeted by attackers due to their elevated privileges. Entra ID provides a list of recommended roles, including Global Administrator, Application Administrator, and Security Administrator, where MFA should be mandatory. Organizations can choose to include or exclude additional roles based on their specific requirements. Organizations are recommended to omit emergency access or break-glass accounts from these policies.
Blocking legacy authentication protocols:
Legacy authentication protocols, such as POP3 or IMAP, are less secure than modern authentication methods, and attackers may exploit vulnerabilities in these protocols to gain unauthorized access. To reduce the risk of account compromise and enhance overall security, organizations can create a Conditional Access policy that blocks sign-ins via legacy protocols. This policy can be configured to apply to specific roles, such as Global Administrator, Application Administrator, and Security Administrator, where MFA should be mandatory. Organizations can also choose to include or exclude additional roles based on their specific requirements. By blocking legacy authentication, organizations can significantly reduce the risk of unauthorized access before it is gained.
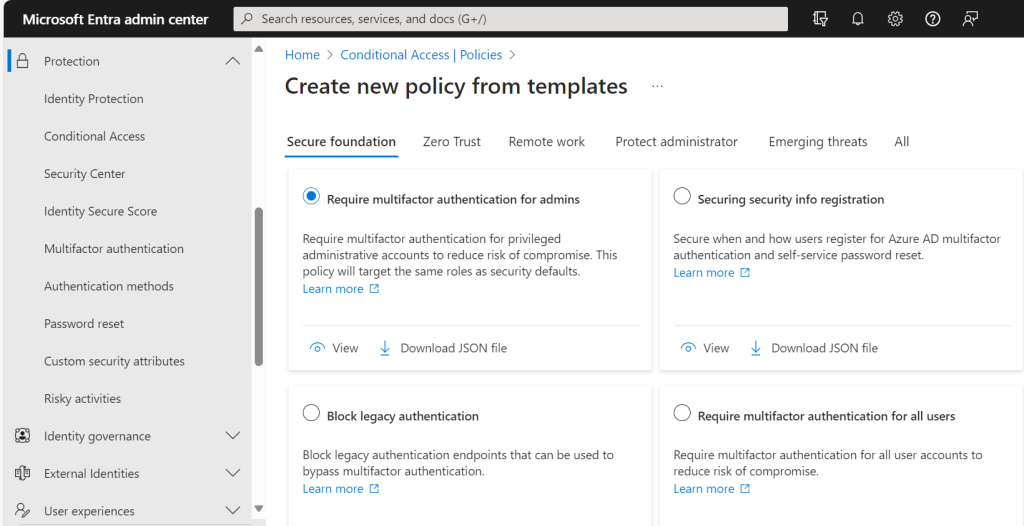
Requiring trusted locations for Azure AD MFA registration:
To enhance the security of Microsoft Entra ID accounts, organizations have the option to enforce the requirement of trusted locations for Azure AD MFA registration. This policy ensures that users can only register for MFA from specified locations, adding an additional layer of protection against potential attacks originating from untrusted locations.
Blocking or granting access from specific locations:
Organizations can use Conditional Access policies to block or grant access based on IP location information, allowing administrators to define trusted IP address ranges to restrict or allow access from specific countries or regions. This provides granular control over access management and can help organizations enforce specific geographic restrictions for accessing resources or allow access only from certain locations. Named locations in Conditional Access policies are a powerful tool for enforcing granular access controls based on the user’s location. These named network locations may include locations like an organization’s headquarters network VPN network ranges, or ranges that you wish to block. Named locations are defined by IPv4 and IPv6 address ranges or by countries/regions. By using these policies, organizations can significantly reduce the risk of unauthorized access and enhance overall security.
Blocking risky sign-in behaviors:
By integrating Microsoft Entra ID Protection with Conditional Access policies, organizations can proactively identify risky sign-in behaviors and respond accordingly. Policies can be configured to force users to change their password, initiate MFA, or block access until manual intervention is actioned by an administrator. This helps prevent unauthorized access and reduces the potential impact of security breaches.
Best practices for implementing Conditional Access policies
Implementing Conditional Access policies requires careful planning and consideration. Here are some best practices to follow:
Regularly review and update policies: It is crucial to regularly review and update Conditional Access policies to ensure their effectiveness and alignment with organizational security goals as threats and requirements evolve.
Utilize risk-based Conditional Access policies: By configuring risk-based Conditional Access policies, organizations can dynamically evaluate the risk associated with each sign-in attempt and adjust access requirements based on the risk level, adding an extra layer of protection against potential cyber threats.
Leverage signals from Microsoft Defender for cloud apps: Integrating Microsoft Defender for Cloud Apps with Conditional Access policies provides additional capabilities in monitoring and managing an organization’s use of cloud services, enhancing visibility and allowing administrators to proactively respond to suspicious activities, thus reducing the risk of data breaches.
Apply policies in a phased approach: Instead of applying policies organization-wide, consider implementing them in a phased approach, starting with a subset of users or specific applications and gradually expanding the scope. This allows administrators to test and fine-tune policies, ensuring minimal disruption to productivity while maintaining a robust security posture.
Monitor and analyze policy impact: Continuously monitor and analyze the impact of Conditional Access policies on user experience, productivity, and security using Microsoft Entra ID’s reporting and analytics capabilities. Use these insights to refine policies and strike a balance between security and user convenience.
This reading has highlighted that Conditional Access policies are a crucial component of a comprehensive security strategy. By leveraging identity-driven access controls, organizations can protect their valuable assets while empowering users to be productive. The reading has also explored additional Conditional Access policy options beyond the basic MFA requirement. Best practices for implementing these policies have been emphasized, including the importance of regular policy review, risk-based approaches, and leveraging signals from Microsoft Defender for cloud apps. By following these guidelines and adopting a proactive stance towards security, organizations can effectively mitigate risks, minimize disruption in the workplace, and enhance their overall security posture.
If you’re interested in implementing Conditional Access policies for your organization, consider reaching out to our company for expert guidance and support. Contact us today to learn more about how we can help you enhance your security posture and protect your valuable assets.

