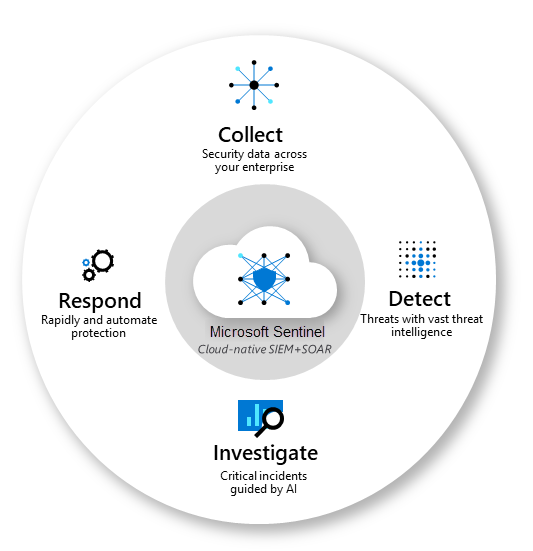
What is Microsoft Sentinel?
Security Information Event Management (SIEM) and Security Orchestration Automated Response (SOAR) product within the Microsoft ecosystem. It empowers organizations with intelligent security analytics and threat intelligence capabilities, serving as a central hub for alert detection, threat visibility, proactive threat hunting, and efficient threat response.
Purposes of Microsoft Sentinel
Microsoft Sentinel serves as your vigilant guardian, offering a panoramic view across the enterprise landscape. It plays a pivotal role in mitigating the challenges posed by the rising complexity of cyberattacks, the surge in alert volumes, and the extended timeframes required for incident resolution.
• Collecting data at a vast cloud scale, encompassing all users, devices, applications, and infrastructure, whether on-premises or in the cloud.
• Discover previously unnoticed threats and reduce false alarms by using Microsoft’s analytics and threat intelligence capabilities.
• Utilize artificial intelligence to probe potential threats and actively search for suspicious activities, leveraging Microsoft’s extensive cybersecurity expertise built up over years of experience.
• React promptly to incidents by employing pre-programmed orchestration and automation for everyday tasks.
Seamless Data Integration
Microsoft Sentinel is equipped with various connectors for seamless integration with Microsoft solutions right from the start. These connectors ensure real-time integration and cover essential components like Microsoft Threat Protection solutions, as well as Microsoft 365 sources such as Microsoft 365 products (formerly known as Office 365), Azure Active Directory (Azure AD), Microsoft Defender for Identity (formerly known as Azure ATP), Microsoft Cloud App Security, and beyond.
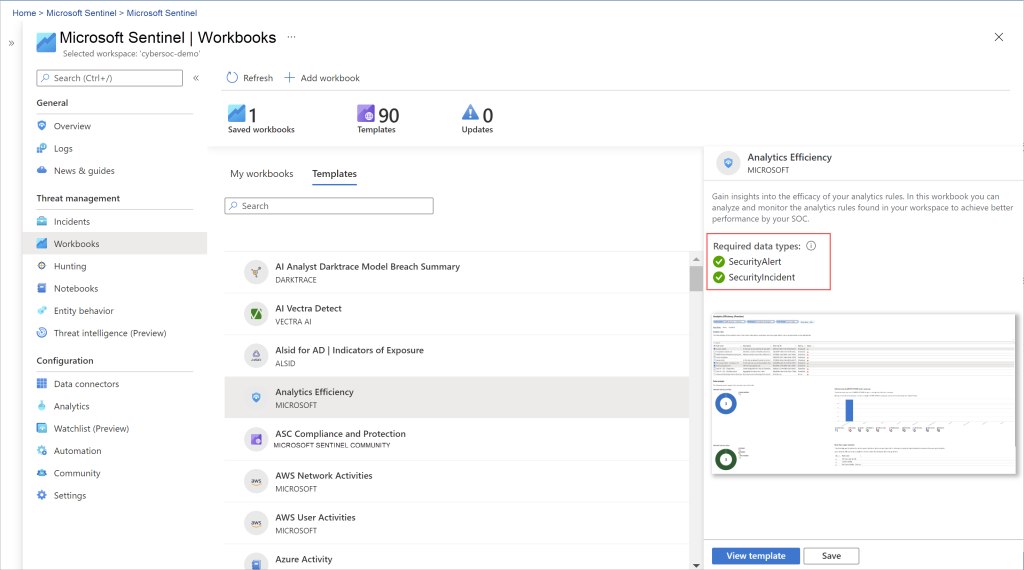
Workbooks
With Microsoft Sentinel, you have the capability to monitor data through the integration of Microsoft Sentinel with Azure Workbooks. This integration offers flexibility in crafting customized workbooks to suit your specific needs.
Analytics
Microsoft Sentinel employs analytics to streamline your workflow by reducing unnecessary noise and minimizing the volume of alerts that require review and investigation. It accomplishes this by correlating alerts into incidents, which are clusters of interconnected alerts. These incidents present actionable potential threats that you can delve into and resolve efficiently.
Security Automation & Orchestration
Streamline your routine tasks and simplify security orchestration through playbooks that seamlessly integrate with Azure services and your existing tools. Microsoft Sentinel’s automation and orchestration solution, built upon the robust foundation of Azure Logic Apps, offers a highly adaptable architecture. This architecture empowers you to scale automation effortlessly, ensuring readiness to tackle emerging technologies and evolving threats effectively.
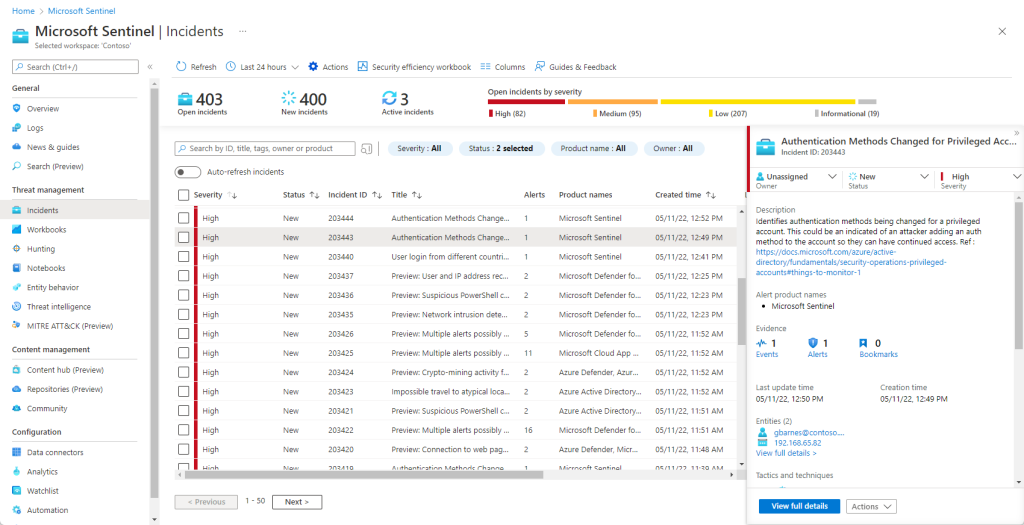
Investigation
Microsoft Sentinel’s deep investigation tools are invaluable for comprehending the breadth and uncovering the root cause of potential security threats. You can utilize these tools to select an entity within the interactive graph, allowing you to pose pertinent questions about that specific entity. This capability enables you to dig deeper into the entity and explore its connections, ultimately pinpointing the core source of the threat.
Hunting
Leverage Microsoft Sentinel’s robust hunting search-and-query tools, which are founded on the MITRE framework. These tools empower you to take a proactive stance in hunting for security threats throughout your organization’s data sources, even before any alerts are triggered.
Community
The Microsoft Sentinel community stands as a formidable asset for enhancing threat detection and automation. The dedicated team of Microsoft security analysts consistently develops and contributes new resources, including workbooks, playbooks, hunting queries, and more. These valuable assets are readily shared within the community, allowing you to leverage them effectively within your own environment.