Microsoft Defender for Cloud Apps functions as a Cloud Access Security Broker (CASB), accommodating various deployment models such as log collection, API connectors, and reverse proxy. It offers robust data travel control and employs advanced analytics to detect and combat cyber threats across all your Microsoft and third-party cloud services.
Defender for Cloud Apps Framework
Shadow IT can be identified and managed: Detect the cloud apps, IaaS, and PaaS services utilized within your organization. Analyze usage patterns, evaluate the risk levels, and assess the business readiness of over 16,000 SaaS apps against more than 80 risk factors. Begin managing these to ensure security and compliance.
Sensitive information can be safeguarded anywhere in the cloud: Identify, classify, and protect sensitive data exposure. Utilize built-in policies and automated processes to enforce controls in real time across all your cloud applications.
Defend against cyber threats and anomalies: Monitor for unusual behavior across cloud apps to detect ransomware, compromised users, or rogue applications. Analyze high-risk activities and automatically remediate them to minimize organizational risk.
Evaluate the compliance of your cloud apps: Determine if your cloud apps adhere to relevant compliance requirements, including regulatory compliance and industry standards. Prevent data leaks to non-compliant apps and restrict access to regulated data.
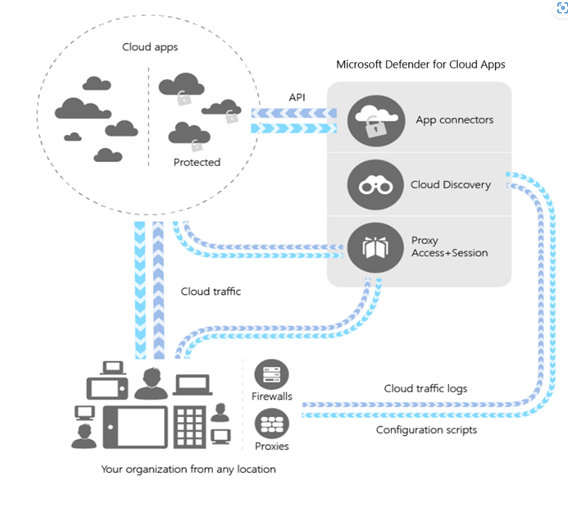
Defender for Cloud Apps integrates visibility with your cloud by
- Cloud Discovery can map and identify your cloud environment and the cloud applications used by your organization.
- Sanctioning and unsanctioning applications in your cloud environment.
- Deploying app connectors to utilize provider APIs, enabling visibility and governance of connected applications.
- Using Conditional Access App Control protection to gain real-time visibility and control over access and activities within your cloud applications.
- Helping you have continuous control by setting, and then continually fine-tuning, policies.
Architecture
Policy Control
- Policies can be used to define users’ behavior in the cloud.
- Use policies to detect risky behavior, violations, or suspicious data points and activities in your cloud.
- You can use policies to integrate remediation processes to achieve complete risk mitigation.
- Types of policies correlate to the different types of information you might want to gather about your cloud environment and the types of remediation actions you might take.
Microsoft Defender for Cloud Apps is a powerful CASB solution that provides comprehensive security for your cloud applications and services. With its advanced capabilities, it helps organizations protect their data, enforce policies, and mitigate risks in the cloud. If you’re interested in implementing this robust solution, our team can guide you through the deployment process and ensure it aligns with your specific security requirements.

