Information security, also known as InfoSec, refers to a range of security measures and tools designed to safeguard valuable enterprise data against unauthorized access, misuse, disruption, or destruction. It encompasses physical and environmental security, access control, cybersecurity, and incorporates various technologies such as cloud access security brokers (CASB), deception tools, endpoint detection and response (EDR), and security testing for DevOps (DevSecOps), among others.
Three pillars of information security: the CIA triad
The CIA triad, which emphasizes confidentiality, integrity, and availability, serves as a framework to guide organizations in assessing risks and establishing systems and security policies.
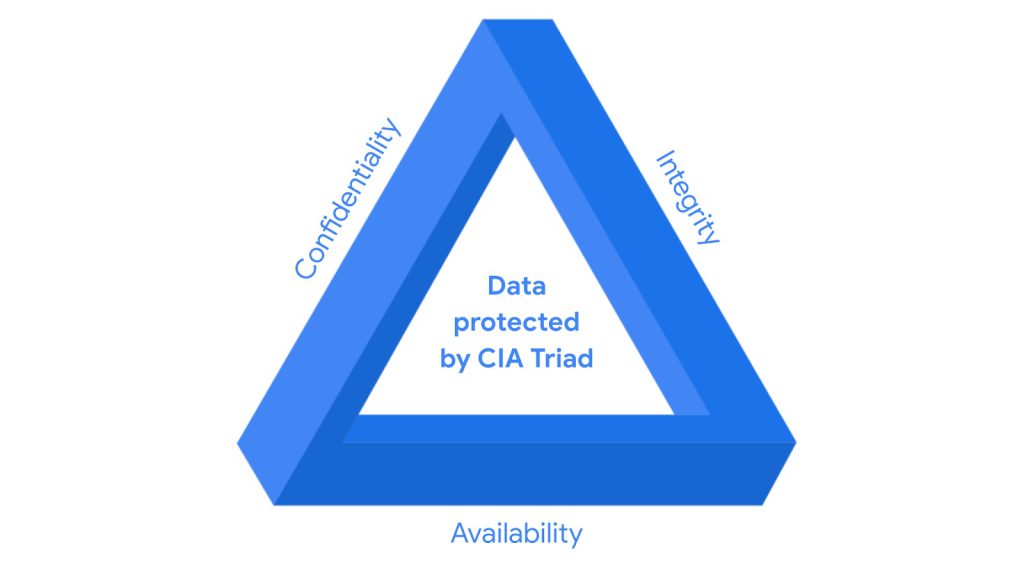
The CIA triad are the three foundational principles used by cybersecurity professionals to establish appropriate controls that mitigate threats, risks, and vulnerabilities.
Confidentiality
Ensuring privacy is a crucial aspect of information security, and organizations should implement measures that restrict access to information solely to authorized users. To maintain data confidentiality, enterprises can utilize tools such as data encryption, multi-factor authentication, and data loss prevention (DLP) techniques.
Integrity
Maintaining data integrity throughout its lifecycle is imperative for enterprises. Organizations with robust information security practices understand the significance of accurate and reliable data, and take strict measures to prevent unauthorized access, unauthorized alterations, or any interference with it. Utilizing tools such as file permissions, identity management, and user access controls plays a crucial role in upholding data integrity.
Availability
Information security encompasses the ongoing task of consistently maintaining physical hardware and conducting regular system upgrades. These practices ensure that authorized users have reliable and uninterrupted access to data whenever they require it.
Common information security threats
Advanced persistent threat (APT) attack
An advanced persistent threat (APT) attack is a highly sophisticated and prolonged cyberattack where an attacker or a group gains unauthorized access to an enterprise’s network and data. These attacks typically occur over an extended period, often remaining undetected, as the attacker continuously targets and infiltrates the network to gather sensitive information or cause damage.
Botnet
A botnet is a network of compromised devices that an attacker infects with malicious code and controls remotely. Once infected, these compromised devices, often referred to as “bots” or “zombies,” can be manipulated by the attacker to carry out various malicious activities, such as launching distributed denial-of-service (DDoS) attacks, spreading malware, or stealing sensitive information. The attacker can remotely command and control the botnet, leveraging the collective power of the compromised devices for their malicious purposes.
Distributed denial-of-service (DDoS) attack
A distributed denial-of-service (DDoS) attack is a type of cyberattack that involves using a botnet or multiple compromised devices to inundate an organization’s website or application with a massive amount of traffic. The aim is to overwhelm the target’s resources, such as bandwidth, processing power, or memory, causing the website or application to become inaccessible or unusable for legitimate users or visitors.
Drive-by download attack
A drive-by download attack refers to a type of cyberattack where a user’s device automatically downloads malicious code without their knowledge or consent when they visit a compromised or malicious website. This attack takes advantage of vulnerabilities in the user’s web browser or plugins, exploiting them to initiate the download.
Exploit kit
An exploit kit refers to a collection of tools and software designed to identify and exploit vulnerabilities in computer systems and web browsers. These kits are used by attackers to automate the process of detecting vulnerabilities and infecting devices with malware.
Insider threat
An insider threat refers to the risk posed by individuals within an organization who have authorized access but may intentionally or unintentionally exploit it to harm or compromise the organization’s systems, networks, and data.
Man-in-the-middle (MitM) attack
A man-in-the-middle (MitM) attack happens when an attacker intercepts and manipulates communication to steal information by impersonating a legitimate user.
Phishing attack
A phishing attack involves the use of deceptive emails, text messages, or other communication methods to impersonate legitimate organizations or users. The purpose is to trick recipients into revealing sensitive information, such as login credentials, credit card details, or personal data.
Ransomware
Ransomware is a type of malware attack where an organization or individual’s data is encrypted, rendering it inaccessible until a ransom is paid. The attackers demand a sum of money, typically in cryptocurrency, in exchange for providing the decryption key to restore the encrypted data.
Social engineering
Social engineering refers to cyberattacks that exploit human interaction and psychological manipulation to deceive individuals or organizations and gain unauthorized access to sensitive information or systems. The attacker uses various tactics, such as baiting, scareware, or phishing, to gain the trust of their victims and trick them into revealing personal or confidential information.
Social media attack
A social media attack refers to cyberattacks that specifically target social media platforms. These attacks aim to exploit vulnerabilities within the platforms themselves or utilize them as delivery mechanisms for malware, phishing campaigns, or other malicious activities.
Viruses and worms
Malicious, undetected malware that can self-replicate across a user’s network or system. Both viruses and worms are designed to cause harm, steal data, or gain unauthorized access to systems. They can remain undetected by antivirus software and pose significant risks to the security and stability of a user’s network or system.
Technologies used for information security
Cloud access security brokers (CASB)
Microsoft Defender for Cloud Apps is a Cloud Access Security Broker (CASB) solution that works across various cloud platforms. It acts as a security policy enforcement point positioned between enterprise users and cloud service providers. CASBs consolidate multiple security policies, including authentication, credential mapping, encryption, and malware detection, among others. They provide visibility and control over data flow, allowing organizations to enforce security measures and combat cyber threats across all their cloud services. CASBs operate across authorized and unauthorized applications and can manage both managed and unmanaged devices, ensuring comprehensive security coverage.
Data loss prevention
Data loss prevention (DLP) involves the implementation of policies, procedures, tools, and best practices to prevent the loss or misuse of sensitive data. Encryption, which converts plain text into ciphertext using an algorithm, and tokenization, which assigns random numbers to data and stores the relationship in a token vault database, are key tools used in DLP.
In Microsoft Purview, you can enforce data loss prevention by defining and applying DLP policies. These policies allow you to identify, monitor, and automatically protect sensitive items across various platforms and applications:
- Microsoft 365 services such as Teams, Exchange, SharePoint, and OneDrive accounts;
- Office applications like Word, Excel, and PowerPoint;
- Windows 10, Windows 11, and macOS endpoints (latest three versions);
- non-Microsoft cloud apps;
- on-premises file shares, on-premises SharePoint, and Power BI.
By implementing DLP policies, organizations can proactively safeguard sensitive data and maintain data security and compliance.
Endpoint detection and response
EDR, or Endpoint Detection and Response, is a security solution that utilizes a set of tools to detect, investigate, and respond to threats on endpoint devices.
In Microsoft Defender for Endpoint, the EDR capabilities provide advanced attack detection in near real-time, enabling security analysts to effectively prioritize alerts, gain visibility into the full extent of a breach, and take necessary response actions to mitigate threats.
When a threat is identified, alerts are generated within the system for analysts to investigate. Alerts associated with the same attack techniques or attributed to the same attacker are consolidated into an incident, streamlining the investigative and response process. This aggregation of alerts simplifies the collective analysis and response to threats for security analysts.

Microsegmentation
Microsegmentation is a security approach that involves dividing data centers into multiple, finely-grained, and secure zones or segments. This helps mitigate risk by limiting unauthorized access and containing potential threats within specific areas.
In contrast to relying on a single, large network pipe for all data traffic, organizations adopting a Zero Trust approach implement network segmentation, creating smaller isolated environments where specific workloads reside. Each segment is equipped with its own ingress and egress controls, reducing the potential impact of unauthorized access on data and systems. This concept of segmentation minimizes the “blast radius” of any security breaches or unauthorized activities.
Microsegmentation goes beyond traditional centralized network perimeters by employing software-defined micro-perimeters for comprehensive and distributed segmentation. This approach provides enhanced security measures and better control over data flows, improving the overall resilience and protection of organizational networks and data centers.
Security testing for DevOps (DevSecOps)
DevSecOps is an approach that involves integrating security practices and measures at every stage of the software development process. It aims to enhance the speed and efficiency of development while simultaneously improving the overall security posture of applications and systems.
By integrating security into DevOps workflows, DevSecOps promotes a proactive and continuous approach to security. It means considering security requirements, threat modeling, vulnerability scanning, and secure coding practices from the initial design phase through development, testing, deployment, and ongoing operations.
DevSecOps emphasizes collaboration and communication among developers, operations teams, and security professionals to ensure that security considerations are addressed throughout the software development lifecycle. By integrating security early on, vulnerabilities can be identified and addressed promptly, reducing the risk of security incidents and enabling faster response and remediation.
Overall, DevSecOps fosters a culture of shared responsibility for security, enabling organizations to deliver software more quickly, reliably, and securely.
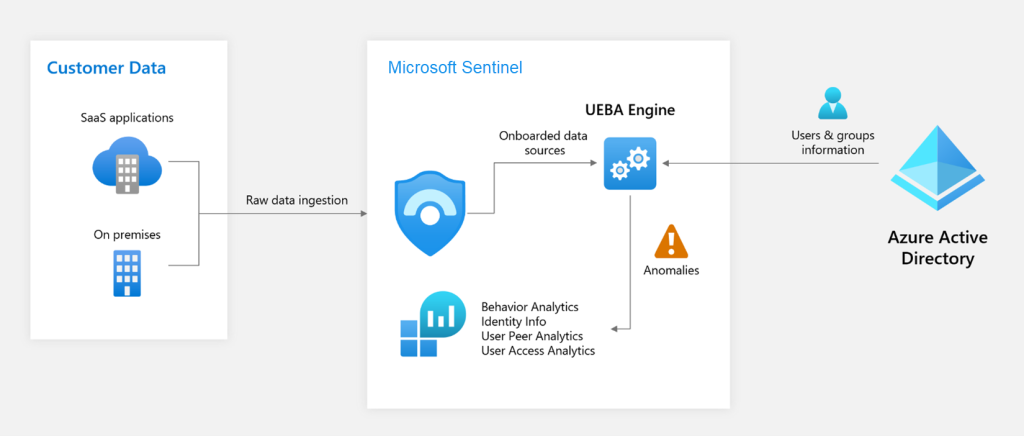
User and entity behavior analytics (UEBA)
UEBA, or User and Entity Behavior Analytics, is a process that involves monitoring and analyzing the typical behavior of users and entities within an enterprise environment. It aims to identify actions and patterns that deviate from normal behavior, helping organizations detect potential threats or malicious activities.
Traditionally, identifying threats within an organization has been a time-consuming and resource-intensive task. Analysts have had to sift through numerous alerts, connect the dots between events, and actively search for potential threats. This process often yields minimal results and can easily miss sophisticated threats like zero-day exploits, targeted attacks, or advanced persistent threats.
The UEBA capability in Microsoft Sentinel streamlines and automates this process, alleviating the burden on analysts and providing them with high-fidelity, actionable intelligence. By leveraging machine learning and advanced analytics, UEBA helps analysts focus their efforts on investigating and remediating potential security incidents, rather than spending time on repetitive tasks. This improves the efficiency and effectiveness of security operations, enabling organizations to better detect and respond to threats within their environment.