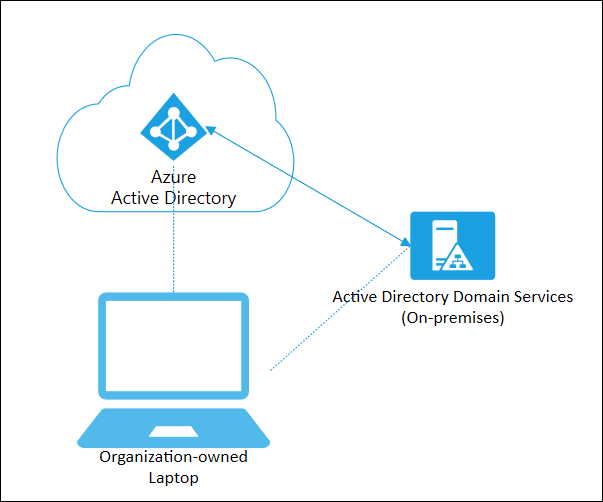
In today’s rapidly evolving digital landscape, organizations strive to seamlessly connect their on-premises infrastructure with the power of the cloud. Microsoft’s Hybrid Azure AD Join emerges as a game-changing solution, enabling businesses to bridge the gap between their local Active Directory (AD) environment and the modern cloud-based Azure Active Directory (Azure AD). This innovative deployment model brings together the best of both worlds, combining the security and familiarity of on-premises infrastructure with the scalability and flexibility of the cloud.
Why hold on to On-Prem AD?
Several main reasons for retaining an On-Prem Active Directory are as follows:
– Legacy Systems and Applications: If an organization heavily relies on legacy systems or applications that are tightly integrated with on-premises AD, it may be challenging or costly to migrate them to a cloud-based AD solution.
– Customization and Control: On-premises AD provides organizations with greater flexibility and control over customization. Some administrative permissions are assigned at the OU level, allowing actions such as enabling/disabling/unlocking users, creating security groups and computer objects, as well as managing Group Policy settings.
– Data Sovereignty: In some cases, organizations may have strict data sovereignty requirements, necessitating that sensitive data, including user credentials, remain within specific geographic boundaries. By retaining an on-premises AD infrastructure, they can maintain better control over where their data resides.
Hybrid – Best of both worlds!
Hybrid Azure AD Join allows users to access both on-premises and cloud resources with a single set of credentials, simplifying the user experience and enhancing security. This powerful integration offers numerous benefits, such as seamless single sign-on (SSO), enhanced security features, streamlined device management, and comprehensive reporting capabilities.
Deploying Hybrid Azure AD Join requires careful planning and execution to ensure a smooth integration of on-premises Active Directory with Azure AD.
In this article, we will outline the main steps to consider for a successful Hybrid Azure AD deployment.
Step 1: Assessing Your Environment
Replication: Verify proper replication between domain controllers using tools like “repadmin” or “Active Directory Replication Status Tool”.
Time Synchronization: Check time synchronization service across domain controllers for accurate authentication and AD operations.
Trust Relationships: Ensure active and functional trusts between forests using tools like “NLTest” or PowerShell cmdlets.
Domain Controller Health: Assess overall health by checking event logs, monitoring resources, and reviewing essential services.
AD Database and System State: Regularly check integrity and test restoration of AD database and system state backups.
Group Policy Objects (GPOs): Review GPO health and consistency for errors or inconsistencies using tools like “Group Policy Management Console” or PowerShell cmdlets.
DNS Configuration: Verify accurate DNS configuration on each domain controller to ensure proper name resolution and no DNS-related issues affecting AD operations.
Step 2: Preparing Your On-Premises Active Directory
To prepare your on-premises Active Directory for Hybrid Azure AD, you need to ensure it meets certain prerequisites. This includes ensuring that the forest functional level is at least Windows Server 2008 R2 and that all domain controllers are running supported versions of Windows Server. Additionally, it is recommended to deploy Azure AD Connect, a tool that synchronizes on-premises Active Directory with Azure AD, ensuring seamless identity integration.
Step 3: Configuring Azure AD Connect

Azure AD Connect serves as a critical component in establishing the connection between your on-premises Active Directory and Azure AD. During the configuration process, you need to define the synchronization options, such as the scope of synchronization, filtering rules, and password hash synchronization. It is crucial to follow Microsoft’s best practices and guidelines to ensure a smooth and secure synchronization process.
Step 4: Choose suitable Synchronization Architecture
ADFS (Active Directory Federation Services) – Legacy Choice:
- Enables single sign-on (SSO) between on-premises AD and Azure AD.
This method may not be the optimal choice for most organizations as the overarching trend in modern infrastructures is to minimize the on-premises computing and networking footprint. Implementing this approach typically necessitates the deployment of at least four server machines, which can increase the infrastructure complexity and maintenance overhead.
Password Hash Sync:
- Synchronizes hashed passwords from on-premises AD to Azure AD.
- Allows users to sign in using the same credentials.
- Balances convenience and security.
- Simplifies the user experience while maintaining on-premises password policies.
This method is associated with several security concerns, including password exposure, password policy mismatch, and the risk of credential stuffing attacks.
Pass-Through Authentication:
- Verifies user credentials against on-premises AD in real-time.
- Does not store passwords in Azure AD.
- Offers a seamless sign-in experience.
- Requires reduced infrastructure compared to other methods.
This method addresses the existing concerns regarding passwords being replicated outside of the on-premises AD. However, the functionality of Office 365 and other AD-integrated applications relies on a continuous connection between the company’s network, which hosts the Domain Controllers, and the Internet. If the data center hosting the Domain Controllers were to lose internet connection, it would result in the paralysis of all Azure AD Integrated Applications, including Office 365.
Step 5: Implementing Privileged Access
Once the Hybrid Azure AD deployment is in place, it becomes crucial to enforce robust security measures and implement conditional access policies. One important consideration is determining the approach for Privileged Access, which involves choosing between granting elevated rights to existing accounts (such as Domain Admin Accounts) or creating separate cloud-only accounts for all elevated access. Making a well-informed decision in this regard is vital to maintain the security and integrity of the Hybrid Azure AD environment. The most popular security practice is to create cloud-only accounts for administrative functions on the tenant and use PIM to provide “Just Enough and Just In-Time” elevation model.
Step 6: Monitoring and Maintenance

Ongoing monitoring and maintenance are crucial for the success of a Hybrid Azure AD deployment. Regularly review logs, monitor synchronization status, and proactively address any issues or anomalies. Stay updated with Azure AD releases and security advisories to ensure you’re leveraging the latest features and mitigating potential risks.
Deploying Hybrid Azure AD Join requires careful planning and execution. By considering these main steps, you can successfully integrate your on-premises Active Directory environment with Azure AD, enabling seamless user experiences, enhanced security, and centralized management across hybrid environments. Remember to consult Microsoft’s official documentation and seek professional assistance if needed during the deployment process.
These are the general concerns for Hybrid Azure AD Architectural Considerations. Stay tuned for part II, which will delve into detailed technical troubleshooting tips for implementing the Hybrid Azure AD environment.